Making 2024 Your Year of Edge Security and Performance
We’ve written about “The Edge.” We defined it not as a location, but as an overall customer and user experience when interacting with your company. Successful edge networking ensures performance and security when your data, users, and customers are widely distributed.
Your employees may no longer work at your headquarters, or in an office at all. They may be at home, they’re in a coffee shop, they’re in a remote location, or they’re in transit. They may no longer use only the computer assigned by your company, but their own laptops, smartphones, and tablets. Your applications, platforms, and data are already hosted in multiple public cloud environments. This is in addition to your own private hosted cloud, and your employees need access to all of it.
On top of that, your customers demand an exceptional experience no matter how they access your goods or services. Keep reading this SASE guide to see how you can achieve that.
What is SASE? Secure Access Service Edge Explained
What does SASE mean? SASE (pronounced “sassy”) is the combination of security and networking elements offered in a single package. SASE combines comprehensive SD-WAN capabilities with complete network security functions such as SWG, CASB, FWaaS, and ZTNA. These elements support the dynamic, growing, distributed security needs of companies everywhere.
The SSE solution leverages the Cloud, so there’s no need to purchase new hardware. Plus, it’s managed by your vendor. This means that there’s no need to hire specialized security or IT staff to manage it. SASE is a networking package that includes connectivity (“SA” or the “secure access”) and security (“SE” or the “service edge”). The diagram below presents our model.
This is complex stuff.
Secure Access Service Edge or SASE architecture hangs on the Cloud and is customized to secure your highly distributed environment.
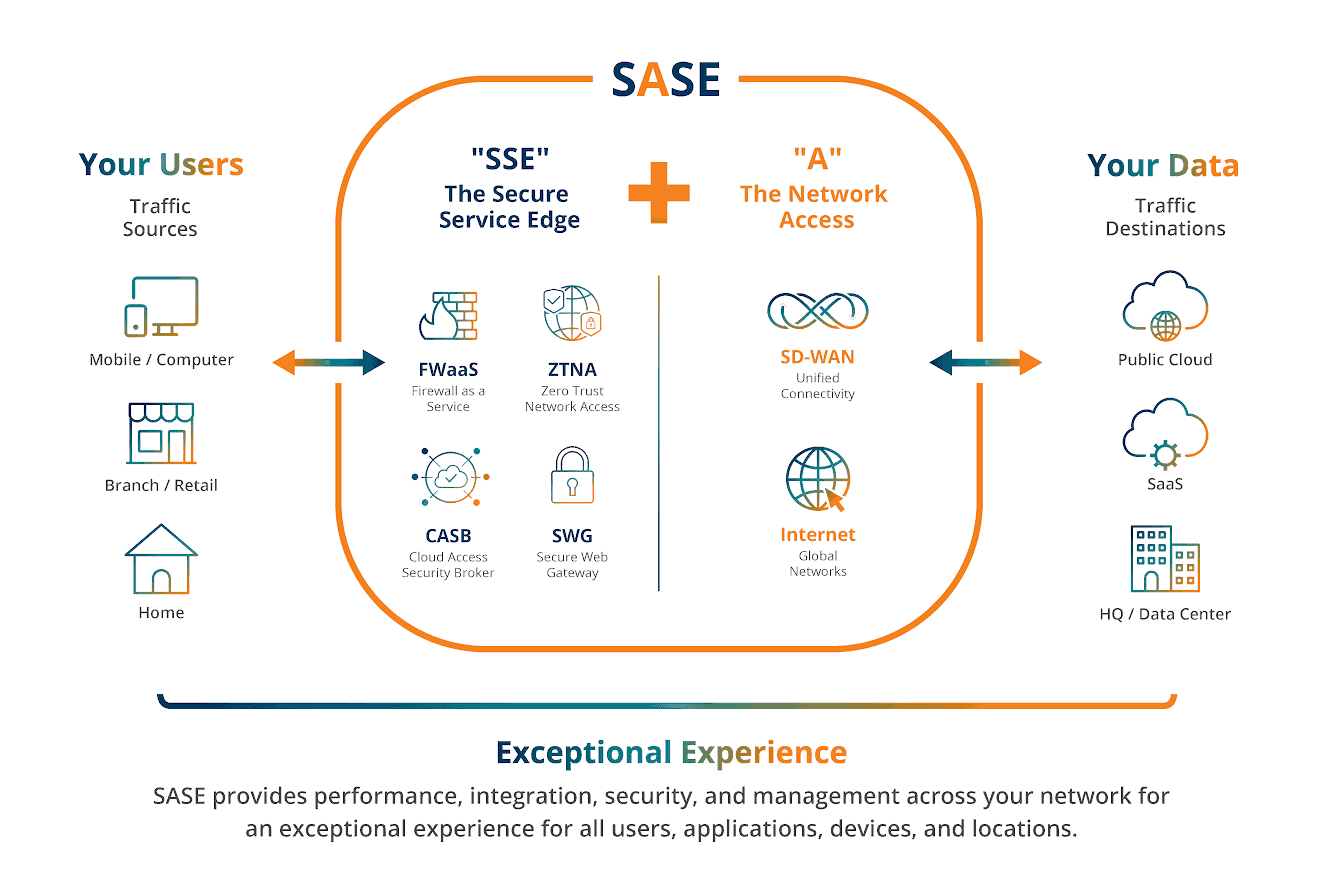
How does SASE work?
Let’s dive into the specific components of SASE (Secure Access Service Edge) to better understand how it works.
The “SSE” part of SASE is the Secure Service Edge. This is the core package of security components that will protect your data, your applications, and your users.
The four key elements of security service edge (SSE) are Firewall as a Service (FWaaS), Zero Trust Network Access (ZTNA), Cloud Access Security Broker (CASB), and Secure Web Gateway (SWG). These elements are presented in greater detail below.
While any of these security services can be purchased separately, they work more efficiently as part of an integrated SASE solution.
1. Firewall-as-a-Service (FWaaS)
The explosion of applications and users everywhere can mean that you’re managing hundreds or thousands of firewalls to ensure security. If you’re routing all user traffic through a centralized point (such as a data center) because that’s where your firewall is located, user performance and security suffer.
Firewall-as-a-Service, also known as cloud firewall, places the management burden on your vendor. FWaaS delivers firewall functionality as a cloud-based service.
Good FWaaS offerings provide the same features as a next-generation firewall. SASE offers FWaaS as part of a unified, cloud-based security model. This way, you can easily manage deployment from a single platform.
2. Zero Trust Network Access (ZTNA)
ZTNA, another component of your SASE solution, is an ideal security approach for your distributed environment. When ZTNA is employed outside of the SASE environment, users must first authenticate through a gateway to gain access to an application.
This authentication occurs no matter where the user is located, no matter the device or network access they’re using. ZTNA focuses on policy, identity and content. The policies follow the identity of each user wherever they are, and the control is yours. ZTNA is zero trust – meaning that it adopts a “least privilege” strategy. No access is permitted until you say it is. Security administrators identify users and create policies to restrict or allow access, minimize data loss, and quickly mitigate potential threats. ZTNA inspects and logs all traffic, and strictly enforces access control.
When ZTNA is offered as part of a unified SASE package, SASE applies the security principles across other services within the SASE solution. By accurately identifying users, devices, and applications, no matter where they are connecting from, you have simplified policy creation, policy management, and rules enforcement.
Connecting through a gateway adds complexity to the security solution. ZTNA through SASE removes the complexity of the gateway connection. It does this by incorporating required networking and security services into a single cloud framework.

3. Cloud Access Security Broker (CASB)
CASB is another essential security component of SASE. It secures traffic between an enterprise and its cloud providers. CASB comprises data security, threat protection, data loss prevention, and application control. And, crucially, it includes pre-configured government compliance for financial and healthcare organizations.
CASB creates a single platform for administrators to manage security controls for all application types. When CASB is integrated into a SASE solution, it works much better than CASB alone. With a unified SASE solution, CASB provides the visibility that helps you understand which software apps are being used and where sensitive data is going, no matter where users are located.
4. Secure Web Gateway (SWG)
If your organization already runs centralized web filtering to prevent access to certain inappropriate web destinations, you have an incomplete solution. Because web filtering runs on a separate appliance, it results in inconsistent policy enforcement when your employees are working remotely. Further, web filtering only looks at web-based traffic and ignores non-web applications and data traffic. This can leave your company exposed.
SWG with SASE fixes this. SWG includes a comprehensive web security solution. This includes SSL Proxy, URL Filtering, Intrusion Detection and Prevention (IDS/IPS), NextGen Anit-Virus (NG-AV), Data Loss Prevention, and Advanced Threat Protection.
With SWG as part of your SASE security package, you have complete visibility and control over traffic, regardless of employee locations. As you grow, your SWG automatically scales to continue supporting you.
You enjoy overall control of your policies and visibility into their enforcement. Still, you need not hire an army of IT and security experts to start to take advantage of SASE. The service is already tailored to your highly distributed environment.

SD-WAN vs. SASE
The “A” part of SASE is the network access – your WAN connection to the security services presented above. As your corporate perimeter dissolves when applications move to multiple clouds to be accessed from anywhere, you must offer end users seamless connectivity and security. An SD-WAN “overlay” to your public Internet or private WAN network optimizes your WAN, unifies security across users, and saves money.
The network access includes the following elements:
- The SD-WAN overlay, including its self-healing architecture and AI operations
- The global SASE POPs
The many benefits of SD-WAN are widely documented, and summarized again here:
1. SD-WAN improves digital experiences
SD-WAN provides application-aware routing, no matter the origination or destination of the traffic. This means that the network is always available for your critical applications, as defined by you, even for your most remote users and locations. If the site has connectivity, even just an Internet connection, it can be integrated into your corporate SD-WAN.
2. SD-WAN is easy to adopt and integrate
Deployment is pre-configured, automated, and centrally provisioned. This allows for faster installations and eliminates the need for dedicated project managers at your remote sites.
3. SD-WAN really performs
SD-WAN includes AIOps data correlation. This automates root cause analysis leading to faster diagnoses. Further, automated workflows learn the network to deliver proactive remediation, improving uptime. If your organization already has the SD-WAN network connection, then the “SSE” portion of SASE is all you need. If your organization already has a private WAN, consider an SD-WAN overlay. SD-WAN allows you to redirect some traffic to your broadband Internet links without disrupting or modifying your WAN.
This saves your WAN for applications that require private connections for compliance and accelerates the performance of all of your traffic. This improves your observability, visibility, and control.
The global SASE POPs are locations of interconnection between your sites and the SASE service. They are the initial point of security and processing for your end-users’ traffic. You’ll hear SASE providers brag about the number of POPs they offer globally and how widely distributed those POPs are.
And for good reason. The more numerous, widely distributed, and optimally placed the POPs are, the closer users are to the SASE solution and to the cloud services being accessed. This proximity lowers latency and provides better overall performance of the service.

Why do I need SASE?
We’ve discussed the benefits of SASE throughout this blog. However, put simply: SASE provides an unmistakable return on investment (ROI).
SASE architecture boosts the performance of your inexpensive broadband connections and eliminates costly hardware and operational investments. What’s more, it ensures the security of every remote, hybrid, and office worker. It also gives you a full understanding of how your network and applications are performing.
Usually, cost savings are achieved by cutting corners and compromising on things like network performance. With SASE architecture, the value that results from improved performance turns into an overall lower total cost of ownership (TCO). Summarized, SASE accomplishes long-term ROI by:
- Simplifying and unifying your edge-to-edge security, reducing the operational expense of managing multiple vendors, platforms, and security systems.
- Providing consistent, policy-based security and data protection where you define the policies, and your vendor applies and manages them.
- Easily scaling to grow as you grow. This means faster integration of new people, locations, and applications which translates to faster realization of business results. And time is indeed money.
- Including your SD-WAN overlay on top of your current access – no need for expensive new network connections.
- Improving overall network performance, with less time chasing vendors and repairing impairments or outages.
- Keeping all communication secured regardless of network location. ZTNA follows the person to ensure that the identity of that person, rather than their physical network location, is used to ensure trusted access.
2024 is the time for a truly unified security and WAN solution
The addition of SD-WAN or SASE need not occur all at once – removing the risk from this change. As you explore SD-WAN and decide you love it, we can easily connect new locations by shipping pre-configured edge hardware in a plug-and-play mode. API integration with your ITSM ensures we stay in sync, providing better two-way ticketing and status visibility.
Zayo designs a tailored solution to meet your unique business needs – greenfield or takeover, regardless of how many vendors you have in your network. With industry-leading management and security, you can safeguard your network security threats, meet regulatory compliance requirements, and enable seamless and scalable hybrid work. Zayo is the one single-managed solution that provides the best breed of SD-WAN and SSE fully managed by us.
Why is Zayo the best managed service provider for you?
- Onboarding: We take the time to get things right before we deploy. We bring the network experts to the table and discuss your project’s dependencies, goals, users, and expectations. Armed with this information, we design the project plan. You always have direct access to your Zayo team, ensuring a smooth end-to-end network transformation.
- Day 2 support: Zayo easily adapts to your unique needs. We can manage third-party circuits and contact providers directly. With a customized NOC playbook designed for success when the unthinkable could go wrong, we make certain you feel comfortable with your current deployment, network AIOps platform, and future digital transformation goals.
- AIOps platform & zInsights: Our AIOps platform is the brains behind your network’s operations. It’s the difference between a smart device sitting on your counter and a completely built-in smart-home system. Zayo’s intelligent network system watches your network, predicts when something will go wrong, and then does something about it. The zInsights portal provides insights on end-to-end application and device performance for all your sites and networks. You’ll see how the network responds to performance issues, assigning bandwidth dynamically to the applications demanding it, in real-time. This prevents outages and keeps that company-wide CEO-hosted Zoom call rolling.
- Vendor-agnostic designs: We won’t ever force you into a one-size single vendor solution. We take the best-in-class vendors like Netskope and other SASE and SD-WAN providers to advise and tailor the best solution for each customer.
- We can deploy thousands of locations in days: We do this using automation to enable scaled, rapid deployment without human configuration errors, but with a dedicated project manager.
Our solutions are designed to meet you where you are today and connect what’s next for your business. Let’s make 2024 the year of your unified network, staff, and data security.
